Major public-facing companies have fallen victim to unauthorized individuals gaining access to sensitive data. Here are three famous cases which describe on the result of an authorized person gaining access or someone not being careful while granting access to the most sensitive data.
Case 1 – Pennsylvania Department of Education — mis-assigned permissions
In February 2018, an employee in Pennsylvania’s Office of Administration committed an error that subsequently affected the state’s Teacher Information Management System (TIMS). As reported by PennLive, the incident temporarily enabled individuals who logged into TIMS to access personal information belonging to other users, including teachers, school districts, and Department of Education staff. In all, the security event is believed to have affected as many as 360,000 current and retired teachers.
https://www.venafi.com/blog/7-data-breaches-caused-human-error-did-encryption-play-role
Case 2 – Dallas police department database leak caused by employee negligence
In a series of instances in March and April 2021, the city of Dallas suffered massive data losses because of employee negligence. An employee deleted 8.7 million important police files that the Dallas Police Department had collected as evidence for its cases: video, photos, audio, case notes, and other items. Most of the deleted files were owned by the family violence unit.
https://www.ekransystem.com/en/blog/real-life-examples-insider-threat-caused-breaches
Case 3 – Sage – unauthorized access
Customer data was compromised, causing reputational damage to the organization. Shares in Sage fell by as much as 4.3 percent after the incident occurred. An employee of the firm gained unauthorized access to the employee data of hundreds of UK firms by using an internal login.
https://www.doherty.co.uk/blog/data-breach-examples-rethink-your-data-strategy
As more social and economic activity goes digital, the necessity of privacy and data protection is becoming more widely understood.
All this shows that there is need of Identity management & Access control.
What is Identity management & Access control?
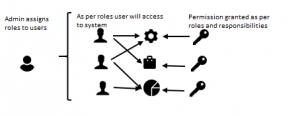
Identity management and access control is the discipline of managing access to enterprise resources to keep systems and data secure.
For example, only a person with the required authority will have access to add, update, or delete data on live servers. And other users will have limited access to the data as per their roles and responsibilities.
It will be the responsibility of IT managers or business owners to control user access to critical information within their organizations and invoke or revoke the access as and when needed.
How do I comply with Access Control?
When I was working on a healthcare project, I was responsible for investigating and resolving any live issues that were reported by the users. If I or the team was unable to troubleshoot the issue by using test data, and if we needed to get access to live data for further investigation, I had to get the permission of the IT manager to access live data. There were stringent rules around access. Access could be granted for 24 or 48 hours. I could not copy the data to any local computer. It had to remain on the protected servers. Once the issue was resolved, my live data access had to be revoked and the IT Manager had to confirm it.
Examples of Broken Access Control
Client-side caching: Browsers store websites in their cache to ensure faster loading if the user tries to access the same website again. This might be a problem if multiple people use the same computer, e.g. in a library or an internet café. Developers should prevent browsers from storing sensitive data in their cache.
Passing Sensitive Data in URL: Let’s say I’m logged in to a website, and my user ID is 228. When I go to my own profile page, the URL looks something like this: https://example.com/profile?id=228. This page might contain sensitive data, which nobody else should see. But what if someone replaces the ID with another user’s ID? So it is important to mask or encrypt the data which we use for passing in the URL.
Why are Identity Management and Access Control important?
Identity management verifies your identity and stores information about you. An identity management database stores your information such as your login id, your job title, and your permissions to access data and authenticates that you are, indeed, the person described in the database.
The stored identity is used by access management to determine which software sets you have access to and what actions you can take when you do.
For example, access management will ensure that the respective manager of each employee has only access to approve leaves.
What Are the Advantages of Identity Management and Access Control?
Identity Management and Access Control ensure that specified users have the access they need to do their jobs while securing sensitive resources and information from unauthorized users.
To conclude, if you do not want your organization to fall victim to loss or misuse of data, giving access to only Authorized Personnel is the first step in data security.





